In Kubernetes, we can decide to prevent certain pods to run in a specific node. We make use of taints and tolerations to achieve this effect.
Taints
What is a taint?
A taints is a key-value pair with a taint effect attached to it. The taint effect can be NoSchedule, PreferNoSchedule or NoExecute .
When the taint effect is NoSchedule, Kubernetes won’t place pods that are intolerant to the taint on the node.
When the taint effect is PreferNoSchedule, Kubernetes will try to not place pods that are intolerant to the taint on the node.
Taint effect NoExecute is more powerful. When such taint effect is set, Kubernetes will evict running pods that are intolerant to the taint on the node and won’t place new pods into the same node.
How do we place a taint on a node?
kubectl taint node name-of-node key=value:effect
aliilman$ kubectl taint node minikube user=me:NoExecute
node/minikube tainted
aliilman$ k describe node minikube | grep Taint
Taints: user=me:NoExecute
Tolerations
What is a toleration?
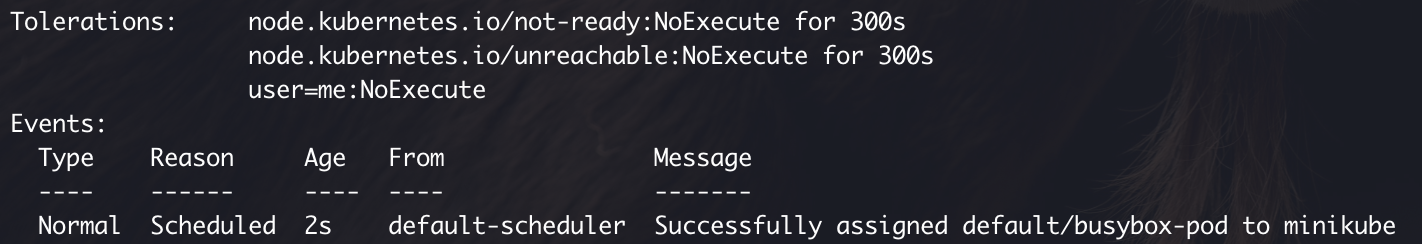
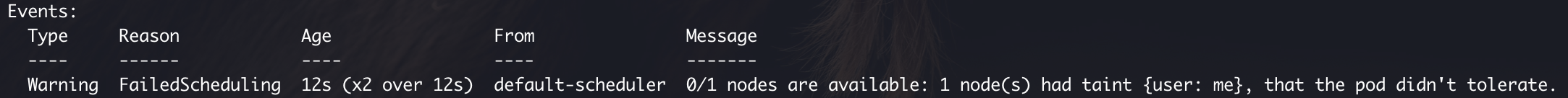
A toleration is something that makes the pod tolerant to taint(s) on the node. This is how the logs will look if a pod is intolerant to the taint placed on the minikube node.
How do we add a toleration to a pod?
apiVersion: v1
kind: Pod
metadata:
name: my-pod
spec:
# containers
tolerations:
- key: 'key'
operator: 'operator'
effect: 'effect'
# When operator is 'Equal'
value: 'value'
# When operator is 'Exists'
# No value property is needed. It basically checks for the existence of the key
So to make the pod in the above screenshot tolerant to the taint on the minikube node, we do this.
tolerations:
- key: 'user'
operator: 'Equal'
value: 'me'
effect: 'NoExecute'